For years, we've been told that long, complicated passwords—filled with random letters, numbers, and special characters—are the key to keeping our accounts secure. But new guidelines from the U.S. National Institute of Standards and Technology (NIST) suggest that this approach is outdated—and may actually make you less safe.
Instead of hard-to-remember combinations, experts now recommend using simpler, more memorable passwords that don’t require frequent changes, according to QBE European Operations.
Why complicated passwords are no longer the best defense
For decades, security policies have pushed users to create unique passwords and update them regularly—often every 60 to 90 days. But according to NIST’s updated SP 800-63-4 guidelines, this method is no longer considered best practice, reported Sprinto.
Instead, NIST suggests:
✅ Updating passwords only when necessary (such as after a security breach).
✅ Avoiding frequent password resets unless there's evidence of compromise.
✅ Focusing on length rather than complexity—long, memorable phrases are better than short, difficult-to-remember ones.

The hidden dangers of overly complex passwords
When passwords become too difficult to remember, people tend to:
🔹 Write them down on sticky notes or in their phone’s notes app.
🔹 Reuse them across multiple sites.
🔹 Store them in browsers or password managers, which can become security risks themselves.
"If a password is too complicated, users are more likely to store it somewhere unsafe," NIST notes.
Hackers often exploit this by targeting saved credentials, making overly complex passwords a liability rather than a strength.
What makes a strong password today?
Instead of complex combinations like Xf9#jS*2!, NIST now recommends using:
✅ A short sentence or a string of random words (e.g., "BlueElephantSky99")
✅ Passwords between 8 and 15 characters
✅ Minimal use of special characters or uppercase letters
NIST’s research found that longer, simple passwords are harder for attackers to guess than shorter, overly complex ones.

What about businesses requiring frequent password changes?
Many organizations still require employees to update their passwords every few months. However, NIST’s Digital Identity Guidelines state that these frequent resets are unnecessary and ineffective.
"The latest changes incorporate real-world security risks and acknowledge that forced password changes do not significantly improve security," NIST explains.
Instead, the agency urges businesses to:
✅ Allow employees to keep passwords longer unless a breach is suspected.
✅ Encourage passphrases instead of short, complicated passwords.
✅ Implement two-factor authentication (2FA) for added protection.
Should you change your password habits?
NIST’s updated guidance challenges traditional cybersecurity rules, but its recommendations are based on real-world data from compromised password databases.
As cyber threats continue to evolve, security experts agree:
✅ Password complexity is less important than length.
✅ Frequent password resets are unnecessary.
✅ Memorable passphrases are better than random characters.
If your workplace or online accounts still enforce outdated password policies, it may be time to push for updated security measures that align with the latest research.












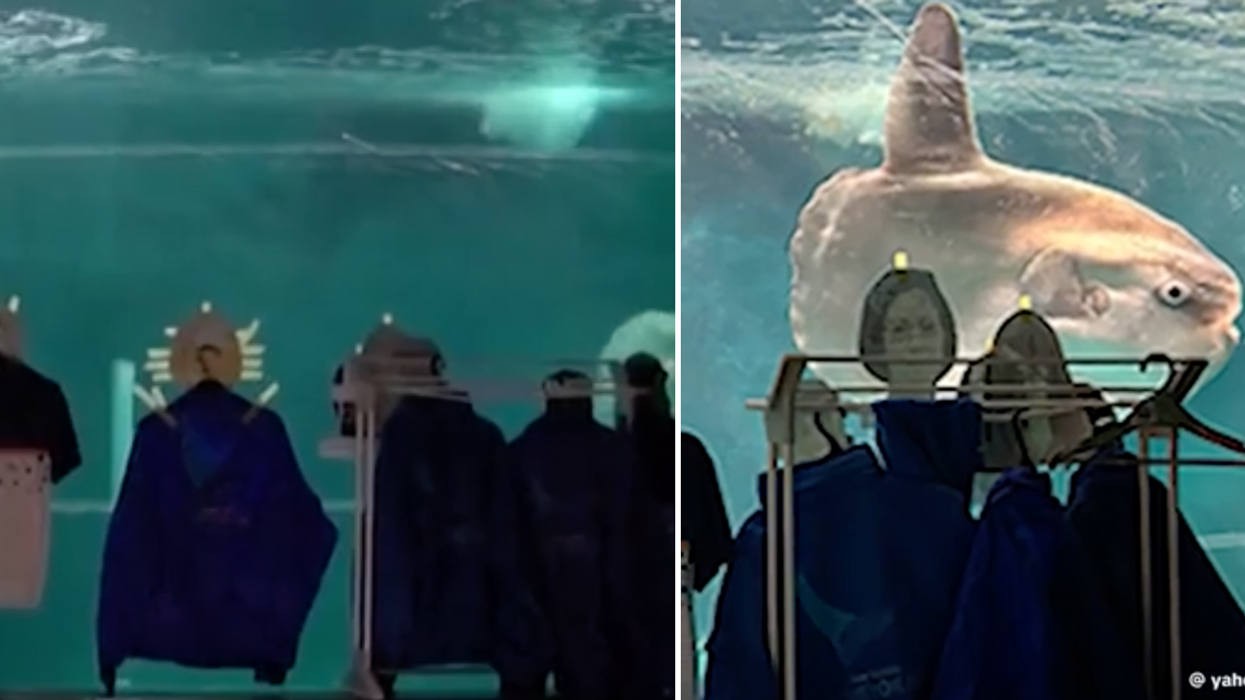

 It wasn't even February, so she wasn't expecting what came next.
It wasn't even February, so she wasn't expecting what came next.  The hug came first, the 'yes' took a few moments more.
The hug came first, the 'yes' took a few moments more. 





 Representative Image Source: Pexels | Oleksandr P
Representative Image Source: Pexels | Oleksandr P 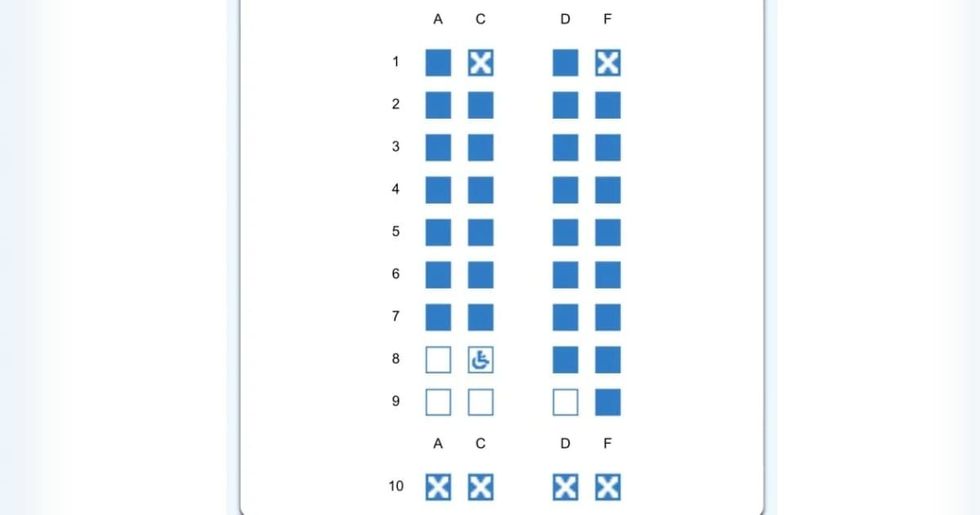 Layout of the plane seatsImage Source: Mumsnet |
Layout of the plane seatsImage Source: Mumsnet | 




 Image Source: Joshua Potash | Reddit
Image Source: Joshua Potash | Reddit 



 Representative photo by luis arias |
Representative photo by luis arias | 
 Representative photo by Jamie Lee |
Representative photo by Jamie Lee | 
